- UNSW
- ...
- Services & support
- Account access & email
- User Access Review
User Access Review
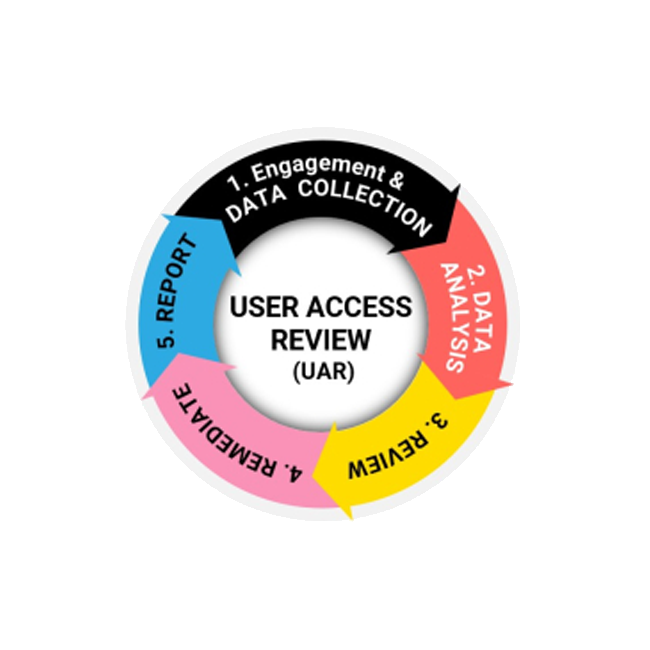
Access Control - UAR
The University's Cyber Security Policies and Standards, opens in a new window require all access to University IT Services to be authorised, restricted based on need, and to be annually verified. Without periodic reviews of user access to applications, the University is at risk of unauthorised access, fraudulent activity, or confidentiality and privacy breaches.
The Cyber Security Guideline - User Access Review, opens in a new window outlines the process, roles, and responsibilities for reviewing access and is a mandatory control required by the Cyber Security Standard - Identity and Access Control, opens in a new window. A UAR revalidates user accounts and access rights associated with IT services and assets.
A UAR cycle involves engagement and data collection, analysis, review (validation), remediation, and reporting.
Current UAR underway
View the applications in scope for the UAR cycle 2024.
-
Communications for a 2024 UAR will be listed here.
The following 2023 UAR messages supported the separate and direct email communications to targeted reviewers:Inside UNSW news:
- Cyber Security Update for April, opens in a new window - announcing the upcoming 2023 UAR.
- Are you across the latest Cyber update for July?, opens in a new window - a reminder to complete pending reviews.
Viva Engage posts:
- UAR begins, opens in a new window with Business Owners (April)
- Review by Managers starts in June, opens in a new window (May)
- Review phase has started, opens in a new window (June)
- Need Help?, opens in a new window Join a UAR Drop-In session (June)
- Last days, opens in a new window - review closes soon (August)
- UAR 2023 is closed, opens in a new window (September)
-
Applications targeted for a 2024 UAR cycle will be listed here.
- Applications in scope for the UAR cycle: 2024
Business Owner is a person with primary responsibility for the business or technology functions provided by one or more UNSW Information Resources, including any associated cyber security risk. Note: The Business Owner of a UNSW Information Resource may be in the UNSW IT unit or any other Organisational unit. Extract from the Cyber Security Standard - Identity and Access Management.
61 applications were part of the 2023 UAR cycle:
Application name Details Business Owner AC Lab System (ACLS MWAC Lab) UNSW Biospecimen service. Carl Power Accept Online Future student admission system. Jason Dolan Active Directory (Privileged Access) A directory service for Windows enabling administrators to manage permissions and control access. Derek Winter Alliances CRM Alliances customer relationship management. Megan Tapia Alumni Experience Chatbot Alumni chatbot. Emily Barton ANZARD Data portal Australian & New Zealand Assisted Reproduction Database. Jade Newman ANZNN Data Portal Australian & New Zealand Neonatal Network Database. Sharon Chow Apply Online Student admission portal for non-UAC applicants. Jason Dolan Astra (Assessment Results) System to submit and process academic results. Jason Dolan Azure AD & Microsoft O365 Azure AD provisions single sign-on access. Microsoft O365 provides software, communication, and collaboration services. Mark Griffith BATS (Bequeathal and Tracking Systems) Management of anatomy donor details, tracking, and ethics. Pascal Carrive BookitLive Issues vouchers for clinic attendance. Belinda Parmenter Calumo Financial administration, budgeting, forecasting, and reporting system. Daniel Chew CASD IT Service Management Tool Request, incident, and problem management system. Mark Griffith Checkmarx Application security testing system. Derek Winter Course Planner - Syllabus Plus Academic timetabling management system. Jonathon Strauss CrowdStrike Managed detection and response service. Derek Winter Data Archives Research Research data archive. Grainne Moran Diligent Board Management system. James Fitzgibbon Echo 360 (Lecture Recording System) Lecture video recording. Dinesh Paikeday eMed Faculty of Medicine web-accessible curriculum management system for the undergraduate program. Gary Velan ERICA (E-Research Institutional Cloud Architecture) Provision of a secure cloud computing environment for research-sensitive data. Louisa Jorm Exam Scheduler - Syllabus Plus Management of examination timetables. Jonathon Strauss Figtree Workers compensation & injury management. Karl Baumgartner Gallagher (Cardax) Building access control system. Tara Murphy Genetec CCTV Closed circuit surveillance system. Tara Murphy GRIS (Graduate Research Information System) Higher Degree Research (HDR) candidature management and workflow administration system. Catherine Zell IBM Storage (Storage Area Network Management IBM ESS Storage) Management of storage subsystems. Mark Griffith ID Health Data Portal Intellectual disability regional health profile system. Julian Trollor InfoEd Research Grants Management System Research Grants Management System. Debbie Docherty Insight CRM Enterprise student customer relationship management system. Jason Dolan Inspera (Digital Assessment Platform) Online assessments and exam platform. Dinesh Paikeday Jaggaer (Chemical Inventory Management) Chemical inventory management system. Karl Baumgartner Katana Computation cluster supporting scientific computing needs of staff and postgraduates. Grainne Moran MidPoint Identity and access management system. Derek Winter Mobius Faculties of Science and Engineering web-based testing system. Jonathan Kress Moodle Learning management system. Dinesh Paikeday MyAccess Virtual application access to specialised applications for academics and students. Dinesh Paikeday MyUNSW Single online access point for UNSW services and information for current staff and students. Jason Dolan NS Financials (New South Financials) Financial administration. Daniel Chew OpenSpecimen (UNSW Biospecimen Services) Biospecimen management system. Anusha Hettiaratchi Physitrack Online exercise program. Belinda Parmenter PIMS (People Information Management System) Human resource and payroll management system. Pete Murray Raisers Edge Fundraising system targeting Alumni. Lindsay Robinson Ramaciotti Computer Cluster & CLIVE Genome sequencing technology system. Helena Mangs RAMS (Records and Archives Management System) Electronic documents and records management system. James Fitzgibbon REDCap (Research Electronic Data Capture) Electronic data capture platform. Grainne Moran ResGate (Research Gateway) Researcher profiles platform. Thomas Chow ResToolkit Research data management and storage system. Grainne Moran ROS (Research Output System) Capture and report on research publications and outputs. Fiona Bradley S4S Audit4 Clinical appointments and billing system. Belinda Parmenter SAM (Software Asset Management) Software asset management system. George Sideris SIMS (Student Information Management System) Student information. Jason Dolan StarRez (Accommodation Portal) Management of UNSW-owned accommodation for students. Isabelle Creagh Thycotic PAM Privileged access management security system. Derek Winter Tivoli Backup Enterprise backup system. Mark Griffith UniHire A talent acquisition and recruitment system for staff and onboarding. Shaun Williams UNSW Press - BC365 Business Central for UNSW Press. David Bridge VARTA Data portal National Perinatal Epidemiology and Statistics Unit Data Portal. Jade Newman Whispir SMS notification service for campus major incidents. Tara Murphy Xetta (OneStop) Conferencing and events management system. Daniel Chew - Application name
- AC Lab System (ACLS MWAC Lab)
- Details
- UNSW Biospecimen service.
- Business Owner
- Carl Power
- Application name
- Accept Online
- Details
- Future student admission system.
- Business Owner
- Jason Dolan
- Application name
- Active Directory (Privileged Access)
- Details
- A directory service for Windows enabling administrators to manage permissions and control access.
- Business Owner
- Derek Winter
- Application name
- Alliances CRM
- Details
- Alliances customer relationship management.
- Business Owner
- Megan Tapia
- Application name
- Alumni Experience Chatbot
- Details
- Alumni chatbot.
- Business Owner
- Emily Barton
- Application name
- ANZARD Data portal
- Details
- Australian & New Zealand Assisted Reproduction Database.
- Business Owner
- Jade Newman
- Application name
- ANZNN Data Portal
- Details
- Australian & New Zealand Neonatal Network Database.
- Business Owner
- Sharon Chow
- Application name
- Apply Online
- Details
- Student admission portal for non-UAC applicants.
- Business Owner
- Jason Dolan
- Application name
- Astra (Assessment Results)
- Details
- System to submit and process academic results.
- Business Owner
- Jason Dolan
- Application name
- Azure AD & Microsoft O365
- Details
- Azure AD provisions single sign-on access. Microsoft O365 provides software, communication, and collaboration services.
- Business Owner
- Mark Griffith
- Application name
- BATS (Bequeathal and Tracking Systems)
- Details
- Management of anatomy donor details, tracking, and ethics.
- Business Owner
- Pascal Carrive
- Application name
- BookitLive
- Details
- Issues vouchers for clinic attendance.
- Business Owner
- Belinda Parmenter
- Application name
- Calumo
- Details
- Financial administration, budgeting, forecasting, and reporting system.
- Business Owner
- Daniel Chew
- Application name
- CASD IT Service Management Tool
- Details
- Request, incident, and problem management system.
- Business Owner
- Mark Griffith
- Application name
- Checkmarx
- Details
- Application security testing system.
- Business Owner
- Derek Winter
- Application name
- Course Planner - Syllabus Plus
- Details
- Academic timetabling management system.
- Business Owner
- Jonathon Strauss
- Application name
- CrowdStrike
- Details
- Managed detection and response service.
- Business Owner
- Derek Winter
- Application name
- Data Archives Research
- Details
- Research data archive.
- Business Owner
- Grainne Moran
- Application name
- Diligent
- Details
- Board Management system.
- Business Owner
- James Fitzgibbon
- Application name
- Echo 360 (Lecture Recording System)
- Details
- Lecture video recording.
- Business Owner
- Dinesh Paikeday
- Application name
- eMed
- Details
- Faculty of Medicine web-accessible curriculum management system for the undergraduate program.
- Business Owner
- Gary Velan
- Application name
- ERICA (E-Research Institutional Cloud Architecture)
- Details
- Provision of a secure cloud computing environment for research-sensitive data.
- Business Owner
- Louisa Jorm
- Application name
- Exam Scheduler - Syllabus Plus
- Details
- Management of examination timetables.
- Business Owner
- Jonathon Strauss
- Application name
- Figtree
- Details
- Workers compensation & injury management.
- Business Owner
- Karl Baumgartner
- Application name
- Gallagher (Cardax)
- Details
- Building access control system.
- Business Owner
- Tara Murphy
- Application name
- Genetec CCTV
- Details
- Closed circuit surveillance system.
- Business Owner
- Tara Murphy
- Application name
- GRIS (Graduate Research Information System)
- Details
- Higher Degree Research (HDR) candidature management and workflow administration system.
- Business Owner
- Catherine Zell
- Application name
- IBM Storage (Storage Area Network Management IBM ESS Storage)
- Details
- Management of storage subsystems.
- Business Owner
- Mark Griffith
- Application name
- ID Health Data Portal
- Details
- Intellectual disability regional health profile system.
- Business Owner
- Julian Trollor
- Application name
- InfoEd Research Grants Management System
- Details
- Research Grants Management System.
- Business Owner
- Debbie Docherty
- Application name
- Insight CRM
- Details
- Enterprise student customer relationship management system.
- Business Owner
- Jason Dolan
- Application name
- Inspera (Digital Assessment Platform)
- Details
- Online assessments and exam platform.
- Business Owner
- Dinesh Paikeday
- Application name
- Jaggaer (Chemical Inventory Management)
- Details
- Chemical inventory management system.
- Business Owner
- Karl Baumgartner
- Application name
- Katana
- Details
- Computation cluster supporting scientific computing needs of staff and postgraduates.
- Business Owner
- Grainne Moran
- Application name
- MidPoint
- Details
- Identity and access management system.
- Business Owner
- Derek Winter
- Application name
- Mobius
- Details
- Faculties of Science and Engineering web-based testing system.
- Business Owner
- Jonathan Kress
- Application name
- Moodle
- Details
- Learning management system.
- Business Owner
- Dinesh Paikeday
- Application name
- MyAccess
- Details
- Virtual application access to specialised applications for academics and students.
- Business Owner
- Dinesh Paikeday
- Application name
- MyUNSW
- Details
- Single online access point for UNSW services and information for current staff and students.
- Business Owner
- Jason Dolan
- Application name
- NS Financials (New South Financials)
- Details
- Financial administration.
- Business Owner
- Daniel Chew
- Application name
- OpenSpecimen (UNSW Biospecimen Services)
- Details
- Biospecimen management system.
- Business Owner
- Anusha Hettiaratchi
- Application name
- Physitrack
- Details
- Online exercise program.
- Business Owner
- Belinda Parmenter
- Application name
- PIMS (People Information Management System)
- Details
- Human resource and payroll management system.
- Business Owner
- Pete Murray
- Application name
- Raisers Edge
- Details
- Fundraising system targeting Alumni.
- Business Owner
- Lindsay Robinson
- Application name
- Ramaciotti Computer Cluster & CLIVE
- Details
- Genome sequencing technology system.
- Business Owner
- Helena Mangs
- Application name
- RAMS (Records and Archives Management System)
- Details
- Electronic documents and records management system.
- Business Owner
- James Fitzgibbon
- Application name
- REDCap (Research Electronic Data Capture)
- Details
- Electronic data capture platform.
- Business Owner
- Grainne Moran
- Application name
- ResGate (Research Gateway)
- Details
- Researcher profiles platform.
- Business Owner
- Thomas Chow
- Application name
- ResToolkit
- Details
- Research data management and storage system.
- Business Owner
- Grainne Moran
- Application name
- ROS (Research Output System)
- Details
- Capture and report on research publications and outputs.
- Business Owner
- Fiona Bradley
- Application name
- S4S Audit4
- Details
- Clinical appointments and billing system.
- Business Owner
- Belinda Parmenter
- Application name
- SAM (Software Asset Management)
- Details
- Software asset management system.
- Business Owner
- George Sideris
- Application name
- SIMS (Student Information Management System)
- Details
- Student information.
- Business Owner
- Jason Dolan
- Application name
- StarRez (Accommodation Portal)
- Details
- Management of UNSW-owned accommodation for students.
- Business Owner
- Isabelle Creagh
- Application name
- Thycotic PAM
- Details
- Privileged access management security system.
- Business Owner
- Derek Winter
- Application name
- Tivoli Backup
- Details
- Enterprise backup system.
- Business Owner
- Mark Griffith
- Application name
- UniHire
- Details
- A talent acquisition and recruitment system for staff and onboarding.
- Business Owner
- Shaun Williams
- Application name
- UNSW Press - BC365
- Details
- Business Central for UNSW Press.
- Business Owner
- David Bridge
- Application name
- VARTA Data portal
- Details
- National Perinatal Epidemiology and Statistics Unit Data Portal.
- Business Owner
- Jade Newman
- Application name
- Whispir
- Details
- SMS notification service for campus major incidents.
- Business Owner
- Tara Murphy
- Application name
- Xetta (OneStop)
- Details
- Conferencing and events management system.
- Business Owner
- Daniel Chew
-
- To complete your review of accesses or view your past UAR cycles, open the MyUAR tool
by clicking on the image or enter: https://myuar.unsw.edu.au, opens in a new window/ into your browser window. - Remember when making a review decision to submit your review before closing the browser window.

2. IT UAR team
- For urgent questions, contact the UNSW IT UAR team via email cybersecurity-uar@unsw.edu.au, opens in a new window.
- To complete your review of accesses or view your past UAR cycles, open the MyUAR tool
-
The following are involved in a UAR cycle:
Involved Responsible for Organisational Unit Heads Ensuring a formal process is in place to manage access rights associated with IT services and assets that are under the units' control. Business Owners Business Owners are responsible and accountable for:
- Ensuring their applications are compliant, with the Cyber Security Standard - Identity and Access Management, opens in a new window, by completing the UAR. Business Owners may delegate this activity to the IT Service Owner, however, the Business Owner retains accountability.
- Scheduling and conducting access control verifications on the applications they are responsible for, as well as being accountable for data collection.
Extract from the Cyber Security Standard - Identity and Access Management.UNSW Managers
(anyone with staff reporting to them, e.g., Supervisors)UNSW Managers, anyone with staff reporting to them, e.g., Supervisors, are responsible for:
- Ensuring their staff access is validated by completing the UAR. Managers may delegate the review activity; however, it is not permitted to delegate a user's access review to the user themselves. In the case of missing manager or supervisor information, the access must be reviewed by the Business Owner.
- Providing, reviewing, and/or removing accounts and/or access for their direct reports.
- Keeping staff up to date on any changes to account access levels.
- Acting as an escalation point for action where they are the Manager Once Removed (MoR).
IT Service Owners
(IT System Owner)IT Service Owners are responsible for:
- Assisting Business Owners by providing user access lists for the applications they are responsible for.
'Information Service Owner means the person responsible for defining, operating, measuring, and improving a UNSW Information Service and associated cyber security controls. Also known as System Owner or IT Service Owner.'
Extract from the Cyber Security Standard - Identity and Access Management.UNSW IT Cyber Security UAR team Oversee the facilitation of a UAR cycle to ensure compliance with Cyber Security Policies and Standards.
- Involved
- Organisational Unit Heads
- Responsible for
- Ensuring a formal process is in place to manage access rights associated with IT services and assets that are under the units' control.
- Involved
- Business Owners
- Responsible for
Business Owners are responsible and accountable for:
- Ensuring their applications are compliant, with the Cyber Security Standard - Identity and Access Management, opens in a new window, by completing the UAR. Business Owners may delegate this activity to the IT Service Owner, however, the Business Owner retains accountability.
- Scheduling and conducting access control verifications on the applications they are responsible for, as well as being accountable for data collection.
Extract from the Cyber Security Standard - Identity and Access Management.
- Involved
- UNSW Managers
(anyone with staff reporting to them, e.g., Supervisors)
- Responsible for
UNSW Managers, anyone with staff reporting to them, e.g., Supervisors, are responsible for:
- Ensuring their staff access is validated by completing the UAR. Managers may delegate the review activity; however, it is not permitted to delegate a user's access review to the user themselves. In the case of missing manager or supervisor information, the access must be reviewed by the Business Owner.
- Providing, reviewing, and/or removing accounts and/or access for their direct reports.
- Keeping staff up to date on any changes to account access levels.
- Acting as an escalation point for action where they are the Manager Once Removed (MoR).
- Involved
- IT Service Owners
(IT System Owner)
- Responsible for
IT Service Owners are responsible for:
- Assisting Business Owners by providing user access lists for the applications they are responsible for.
'Information Service Owner means the person responsible for defining, operating, measuring, and improving a UNSW Information Service and associated cyber security controls. Also known as System Owner or IT Service Owner.'
Extract from the Cyber Security Standard - Identity and Access Management.
- Involved
- UNSW IT Cyber Security UAR team
- Responsible for
- Oversee the facilitation of a UAR cycle to ensure compliance with Cyber Security Policies and Standards.
Important:
- When conducting the review, reviewers (Business Owners, UNSW Managers/Supervisors, or their delegates) are advised to consider that staff may have more than one role across the University, and as a result, it is vital they keep staff informed of any changes as a result of their review.
- Reporting line details for staff have been captured from University HR systems at a point in time. Where Managers identify incorrect reporting relationships as part of this review, they are requested to update details via MyUNSW, opens in a new window or contact the HR Business Partnering team, opens in a new window for assistance.
- There is no immediate action required by staff using applications under review. Any questions about access should be directed to their manager/supervisor.
- Communications will be sent from the Cyber Security UAR mailbox directly to involved Business Owners and reviewers (UNSW Managers/Supervisors) by the Cyber Security UAR Team.
- For full details refer to the Cyber Security Guideline - User Access Review, opens in a new window.
-
User account/ access type Action Duration Escalation
(and duration)Reviewer: Business Owner Privileged accounts - Re-validation of access, or
- Deletion or de-activation of account
Note: Delegate can be an IT Service Owner. Privileged accounts certified by the delegate, must then be re-certified by the Business Owner.
15 working days Manager once removed (MoR)
(10 working days)
Elevated accounts
(IT related)- Re-validation of access, or
- Deletion or de-activation of account.
Note: Delegate can be an IT Service Owner. Elevated access certified by the delegate must then be re-certified by the Business Owner.
Elevated accounts
(Business function-related)- Re-validation of access, or
- Deletion or de-activation of account
Note: Delegate can complete the review.
Reviewer: UNSW Manager (of staff) Standard user account - Re-validation of access, or
- Deletion or de-activation of account
Note: Delegate can complete the review.
15 working days Manager once removed (MOR)
(10 working days)
Important
- Where an assigned UAR has not been completed in 15 working days by the reviewer (Business Owner or UNSW Manager/Supervisor, or their delegate), the Manager once removed (MoR), of the user or account concerned, will be required to complete the UAR in 10 working days.
- Reporting line details for staff (accounts) are sourced, at a point in time, from information in HR systems. To ensure this information is accurate, Managers/Supervisors should review their staff reporting details via MyUNSW, opens in a new window or contact the HR Business Partnering team, opens in a new window for assistance.
- For full details refer to the Cyber Security Guideline - User Access Review, opens in a new window
Past UARs
Completed UARs are summarised below. Official UAR Reports are provided to Business Owners and are confidential. The reports are accessible to internal and external auditors as well as for management reporting. Requests for official UAR Reports are to be made directly to the respective Business Owner.
-
From April to September 2023, an annual User Access Review cycle was completed for 61 University applications. Thirty-four Business Owners and 2,335 Managers/Supervisors and/or delegates (of staff) reviewed 63,709 access permissions pertaining to a total of 18,697 accounts. As a result, 90 percent of the access was certified and retained with 8 percent revoked. Refer to the UAR 2023 summary, opens in a new window for details per application.
-
From March to October 2022, an inaugural User Access Review cycle was completed. The annual user access review targeted 21 University applications. Thirteen Business Owners and 1,550 Managers/Supervisors and/or delegates (of staff) reviewed 39,973 access permissions pertaining to a total of 13,427 accounts. As a result, 86 percent of the access was certified and retained with 11 percent revoked. Refer to the UAR 2022 Summary (PDF, 208KB), opens in a new window to learn more about the applications and survey feedback.

Reporting cyber incidents
It is important to report any cyber security incidents as quickly as possible so that UNSW IT’s Cyber Security team can address any issues and mitigate risk exposure.
What should I report?
- Suspecting your computer or account has been compromised.
- Having evidence on how technology or University data may be vulnerable.
- Noticing a colleague inappropriately sharing Highly Sensitive or Sensitive data.
- Losing a University asset containing sensitive information.
Report a cyber security incident by calling the UNSW IT Service Centre on 02 9385 1333 or using the link below.
Cyber security is everyone’s responsibility and by learning a few rules, simple steps, and following guidelines, we can protect ourselves and our University from cyber security threats and keep data safe. Go to Cyber Security Training and Awareness for more information.
